It’s been an amazing five years working with you, our users, with more than 74,000 deployments across more than 40 releases since we initially shipped Anchore Engine. Today, we are pleased to announce that the project has now reached its 1.0 milestone. Much has changed in the world of container security since our first release, but the need for scanning container images for vulnerabilities and other security risks has been a constant.
Anchore Engine 1.0 includes a focused feature set that is the result of working directly with many organizations toward securing cloud-native development environments and also represents an update to Anchore’s overall approach to delivering DevSecOps-focused open source tools.
New code, New Speed
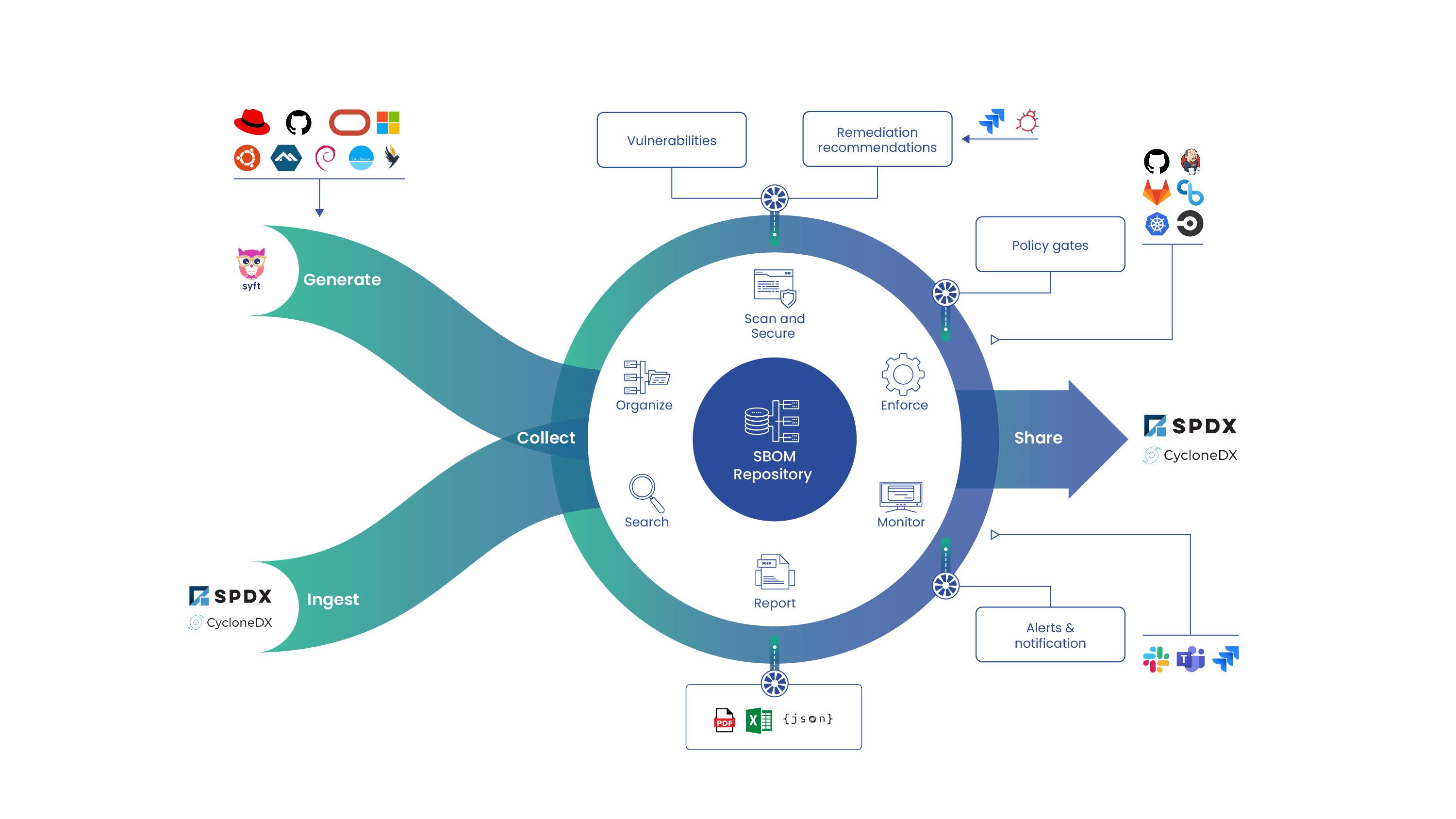
Over and over again, we’ve heard that the three most important criteria for a container scanning tool is that it needs to be quick, it needs to be accurate, and it needs to be easy to integrate into existing development toolchains. To support those needs, last year we took the lessons learned over years of developing Anchore Engine and created two new command line tools: Syft and Grype. Syft generates a high-fidelity software bill of materials (SBOM) for containers and directories, and Grype performs a vulnerability analysis on the SBOMs created by Syft or against containers directly.
With the release of 1.0, we’ve now refactored Anchore Engine to embed these stateless tools for core scanning functions, improving the speed of container image scans and ensuring parity between stand-alone stateless Syft/Grype scans and those produced in the stateful Anchore Engine service. We’ve also cut the time for the initial sync of the vulnerability DB from hours to seconds, getting new users up-and-running even faster than before.
Feed Service Deprecation
Prior to the 1.0 release, deployments of Anchore Engine periodically connect up to our public feed service, hosted in the cloud. The vulnerability data would then be pulled down and merged into your local Anchore Engine database. This merge process often took a while due to the per-record insert-or-update process.
With the new Grype-based scanner, the vulnerability data is now managed using Grype itself using a single file transfer that updates the entire vulnerability database atomically. The vulnerability data itself is generated from the same sources as the public feed service ensuring that you’ll see no drop in distro or package ecosystem coverage. Since Anchore Engine 1.0 will no longer use the public feed service, we plan to sunset the non-Grype feed service on April 4, 2022, which we’ve chosen in order to give all users of Anchore Engine the time to plan and execute upgrades to Anchore Engine 1.0+. After April 4, 2022, any existing deployments of Anchore Engine prior to 1.0 will continue to operate, but will no longer be receiving new vulnerability data updates.
New Tools for CI/CD
When Anchore Engine was created, scanning was centered around the container registry. Now, with GitHub Actions, GitLab Runners, Azure Pipelines, and the ever present Jenkins, scanning in the CI/CD pipeline is fast becoming the norm. We originally created our inline scanner script (inline_scan) to wrap around Anchore Engine and facilitate this workflow, and it did its job well. With Syft and Grype now delivering the same capabilities as inline_scan (and much more), in a faster and more efficient fashion, we are also retiring the project.
As of 1.0, we will no longer be updating inline_scan with new releases of Anchore Engine, and we will stop updating the existing inline_scan images after January 10, 2022. Similarly, our existing native CI/CD integrations based on inline_scan will be or have already been, updated to use Grype internally.
The Road Ahead
Going forward, Syft and Grype will be the best choice for developers and DevOps engineers that need to integrate scanning into their CI/CD pipelines. Anchore Engine 1.0 will continue to play the role of providing persistent storage for the results of CI/CD scans as well as automated registry scanning. Because Anchore Engine 1.0 is built on the common core of Syft and Grype, you will get a consistent result regardless of where you need scans performed and which tools you use.
With the foundational role that SBOMs will play in software supply chain security and the fast moving changes to the various CI/CD platforms, we have an ambitious roadmap for Syft and Grype. Our goal is to make Syft the best open source tool for generating an SBOM and Grype the best tool for reporting discovered vulnerabilities. Anchore Engine will continue to receive updates and improvements, but with registry scanning requirements being relatively static we are not planning any major new capabilities at this time.
Our commercial solution, Anchore Enterprise, will continue to be focused on helping security teams to manage the whole security lifecycle with centralized policy control, audits, and integrations with enterprise platforms. We are committed to ensuring that users who chose to use Syft, Grype and Anchore Engine have a quick and easy path if and when they are ready to make the transition.
Anchore is committed to open source, recognizing that it is the best way to give DevOps teams the tools they need to move fast. Whether you use Syft, Grype, or Anchore Engine, we look forward to working together with you on your DevSecOps journey. You can connect with us on Discourse or GitHub. We’ll also be hosting a webinar on October 20, 2021 to walk you through our open source and enterprise solutions and explain the role and capabilities of each. Register here.
Important Resources
Anchore Engine 1.0
Syft
Grype
Anchore Enterprise
Compare Anchore open source and enterprise solutions
Important Dates
- October 1, 2021 – Anchore Engine 1.0 Available
- October 20, 2021 – Webinar on Anchore open source and enterprise solutions. Register here.
- January 10, 2022 – the inline_scan project will be retired. Users can switch to using syft/grype for stateless security scans. Executions of inline_scan will continue to function but will no longer receive vulnerability data updates. inline_scan will not be updated with Engine 1.0. It will remain on 0.10.x until retirement.
- April 4, 2022 – The public feed service, ancho.re, will no longer be available. Anchore Engine users need version 1.0+ using the v2 scanner to receive new vulnerability data updates. Existing users will continue to function but will no longer receive vulnerability data updates.