Achieve supply chain security with SBOM Management & Automation
High-quality SBOMs enable security teams to scale with their developers. With more visibility, it is easier to secure the open source attack surface and identify open source and third party components in your software supply chain.
Explore Anchore’s approach to SBOM management with a 15 day free trial.
What you get with Anchore
Anchore Enterprise is a modern, SBOM-powered software composition analysis (SCA) tool that identifies every software component in cloud native applications. It provides an end-to-end software supply chain security system with total visibility, deep inspection, automated enforcement, expedited remediation and trusted reporting.
Benefit from end-to-end SBOM management
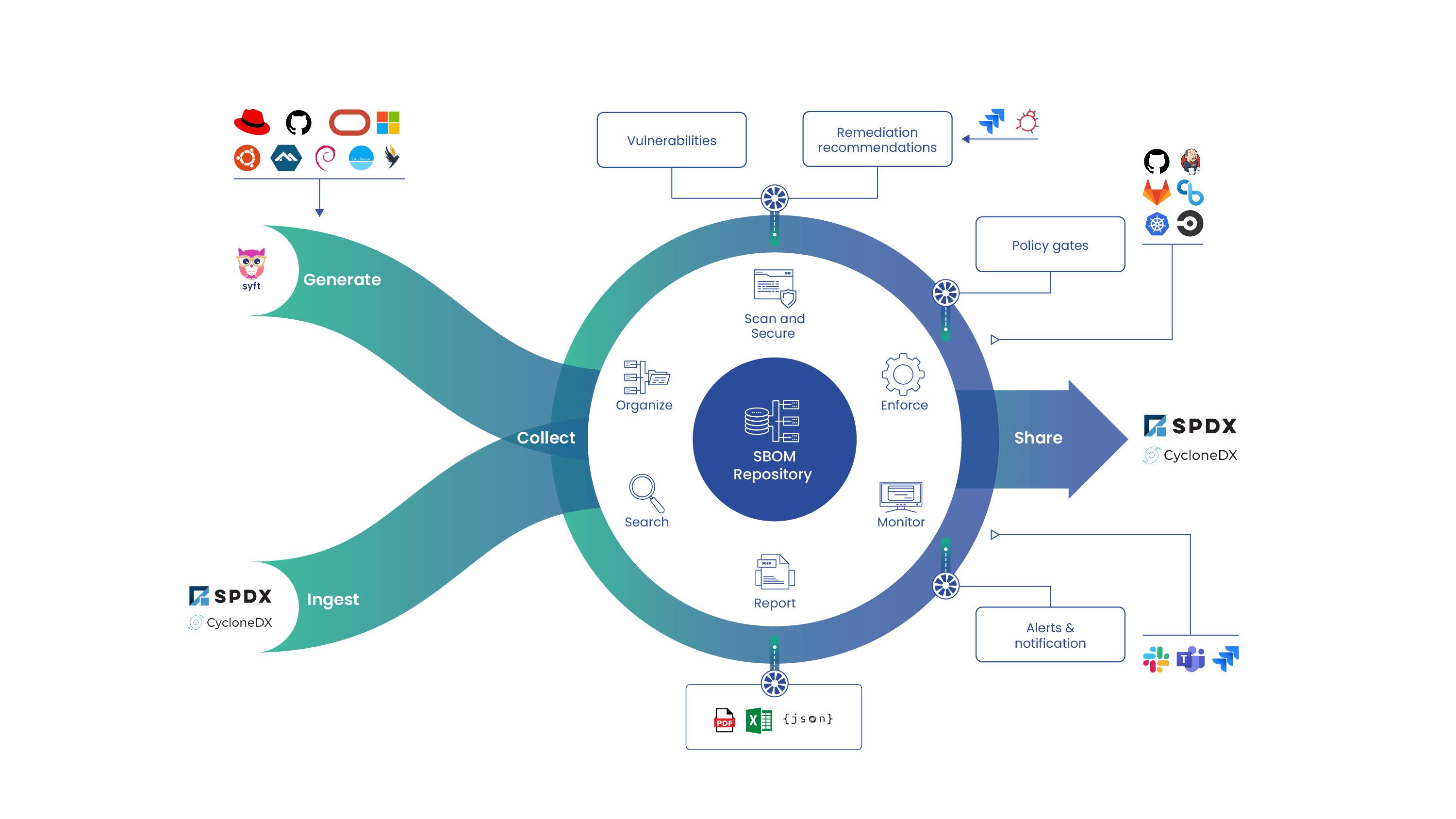
Staying secure and compliant requires continuous, end-to-end insight into your software stack. By generating SBOMs in the development cycle, developers and security teams can identify and manage the software in their supply chains and mitigate issues before they reach runtime. Anchore Enterprise provides end-to-end SBOM coverage so organizations can create a data trail and extended view of the supply chain history of a particular product.


Gain visibility with comprehensive SBOMs
Identify all your software components present in both internally developed and third-party supplied software, including direct and transitive dependencies. Generate SBOMs at each stage in the development process from source code repositories and CI/CD pipelines to container registries and runtimes. Leverage in-depth metadata down to the file level to enforce policy rules.
Respond quickly to new vulnerabilities with an SBOM repository
Keep SBOMs in a centralized repository for complete visibility and ongoing monitoring, even post-deployment. Speed up incident response time for new vulnerabilities — including zero-day vulnerabilities like Log4j — by searching the SBOM repository to easily identify impacted applications.


Track SBOM drift to detect suspicious activity
Detect SBOM drift in the build process to uncover unexpected dependencies, malicious efforts to infiltrate builds, and inadvertent errors. Alert security staff to changes in SBOMs so they can be assessed for risks or malicious activity.
Gain an application-level view of software supply chain risk
Tag and group all artifacts associated with a particular application, release, or service to enable reporting on vulnerabilities and risks. For each new application release, leverage tag-based reporting to pinpoint vulnerabilities for fast remediation.


Identify unsanctioned components with automated SBOM analysis
Define policies based on rich SBOM metadata for packages, files, configuration data, secrets, malware, and more. Get alerted automatically when disallowed software is identified.
Build trust by sharing SBOMs
Produce SBOMs for individual artifacts or entire applications. Easily share SBOMs to external customers, compliance auditors, and internal security teams to build trust about the ingredients of your software.

Why Anchore
Since its inception, Anchore has been putting SBOMs at the heart of our technology and products. Anchore is the creator and sponsor of Syft, one of the most popular open source SBOM generation tools, which has attracted hundreds of developers and thousands of users. This community has helped produce one of the most flexible and accurate SBOM tools in the market.
With this open source tool at its heart, Anchore Enterprise automatically generates and stores SBOMs from every stage of the software development process from source code to runtime, then analyzes for new vulnerabilities to streamline SBOM management.
Anchore Enterprise supports standards such as SPDX and CycloneDX in addition to the richer, native Syft format and enables you to group SBOMs together to accurately reflect the contents of your application.