Kubernetes Image Scanning
Secure your images running in Kubernetes.
Prevent or allow deployment based on flexible policies and continuously monitor running images.
Benefits
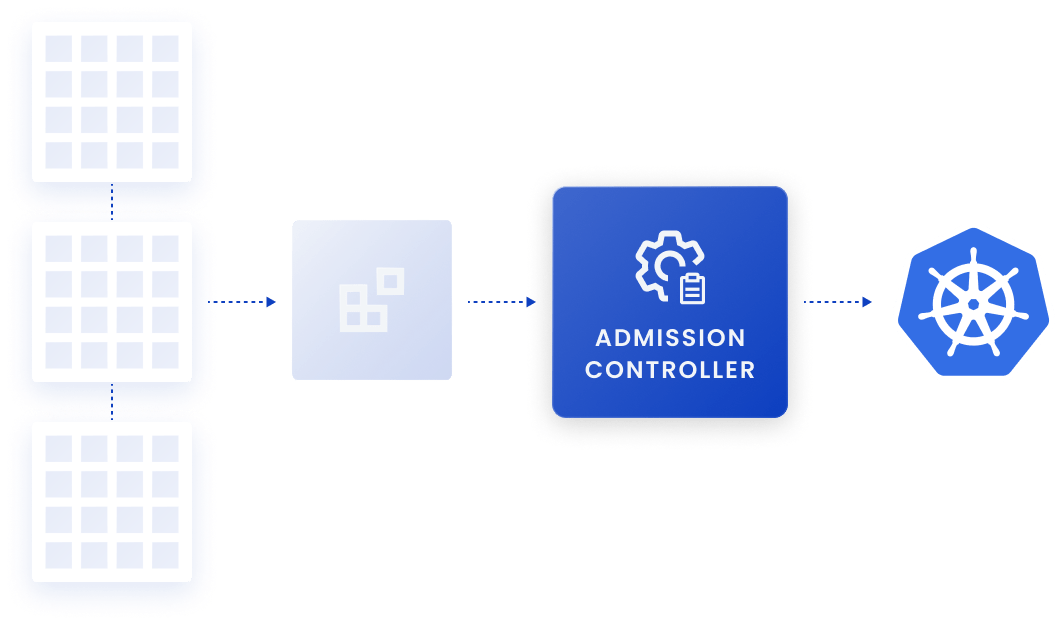
Deploy only secure images.
Prevent deployment of images that don’t meet your organization’s security policies using a Kubernetes admission controller. Set your preferences to ensure that only scanned images are permitted.
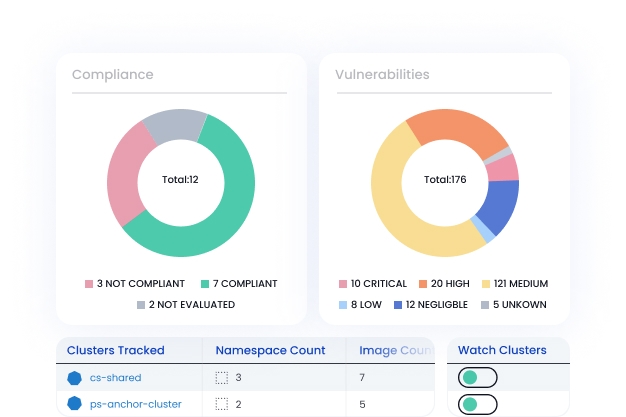
Ongoing visibility.
Easily integrate with Kubernetes to ensure that all running container images have been scanned and monitor for new images.
Continuous container security.
Monitor Kubernetes clusters to identify which vulnerabilities exist in active containers. Quickly identify if a new vulnerability impacts running containers.
How Kubernetes Image Scanning works.
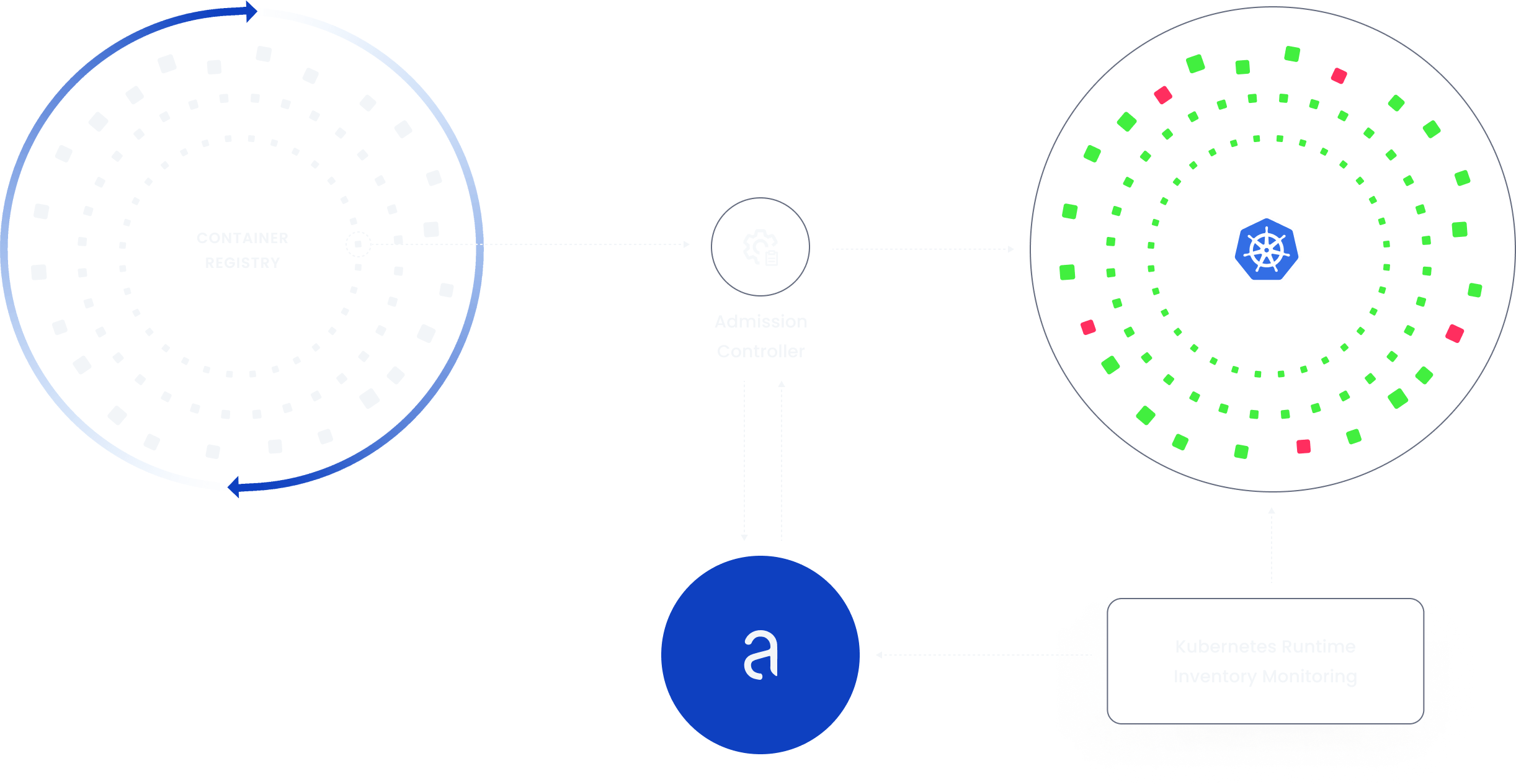

Admission Controller contacts Anchore API for evaluation status.

Anchore inventories running containers and alerts on policy violations.
Related resources.
Visually hidden 

Jan 19, 2022
2022 Software Supply Chain Security Report
Access the Report
Visually hidden 

Sep 08, 2021
Shifting Left and Right: Securing Container Images in Runtime with Anchore
Watch the Webinar
Visually hidden 

Aug 26, 2021
4 Kubernetes Security Best Practices
Read the Blog
Speak with our security experts
Learn how Anchore’s SBOM-powered platform can help secure your software supply chain.
