Secure your DoD software factory with Anchore Federal
Anchore Federal is used across the US Department of Defense (DoD) to secure software factories that speed up development to aid warfighters. With Anchore Federal programs meet DoD DevSecOps requirements, apply zero-trust principles for applications and ensure cyber readiness.
Platform One and Black Pearl are using Anchore to harden containers for the Iron Bank. Anchore Federal is deployed in IL4 and IL6 environments and supports a continuous feed of new vulnerabilities even in an air-gapped or high side environment.
Anchore aligns with the DoD DevSecOps Reference Design and offers:
- Container hardening (Anchore DISA policy pack)
- Container policy enforcement (Anchore Federal policy packs)
- Container image selection (Container Hardening Scanner)
- Artifact storage (Anchore image registry integration)
- Release decision-making (Anchore Kubernetes Admission Controller)
- Runtime policy monitoring (Anchore Kubernetes Automated Inventory)
Anchore is listed in the DoD Container Hardening Guide and the Container Image Creation and Deployment Guide as a Container Hardening scanner.

One of the key purposes of Anchore is the mitigation of insider threat within the DevSecOps lifecycle by detecting unapproved changes to Dockerfiles. Read our latest white paper “DevSecOps for a DoD Software Factory: 6 Best Practices for Container Images” that advises on best practices for setting new standards in security and efficiency for DoD software factories.

Continuous vulnerability scanning
Automate vulnerability scans at each step in the development lifecycle, including source code repos, CI/CD pipelines, container registries, and Kubernetes platforms. Identify vulnerabilities, malware, secrets, and security risks. Anchore Federal integrates with common DevOps platforms such as GitLab, GitHub, or Jenkins to enable a “shift left” security posture and runs on any Kubernetes, including government clouds, on-prem OpenShift or, Rancher.
Automate DoD and NIST security checks
Enforce DoD standards with automated policy checks. Leverage Anchore’s out-of-the-box policy packs for NIST, DoD, DISA, and FedRAMP to speed compliance. Enforce controls for NIST 800-53 and 800-190 out of the box. Demonstrate compliance with controls from the Secure Software Development Framework as codified in NIST 800-218. Uncover issues as the software is built and avoid last-minute surprises before your compliance audit.


Remediate security findings easily
Reduce the manual effort to process security findings and create POA&Ms. Create action plans for developers detailing necessary remediation steps and use time-based allowlists that align POA&Ms. Fix issues faster and smarter.
Provide proof of your security posture
Ensure the security of your software with pass/fail reports of NIST, DoD, DISA, and FedRAMP checks. Document software contents with application-level SBOMs. Track and report on changes in your security posture and SBOMs over time.


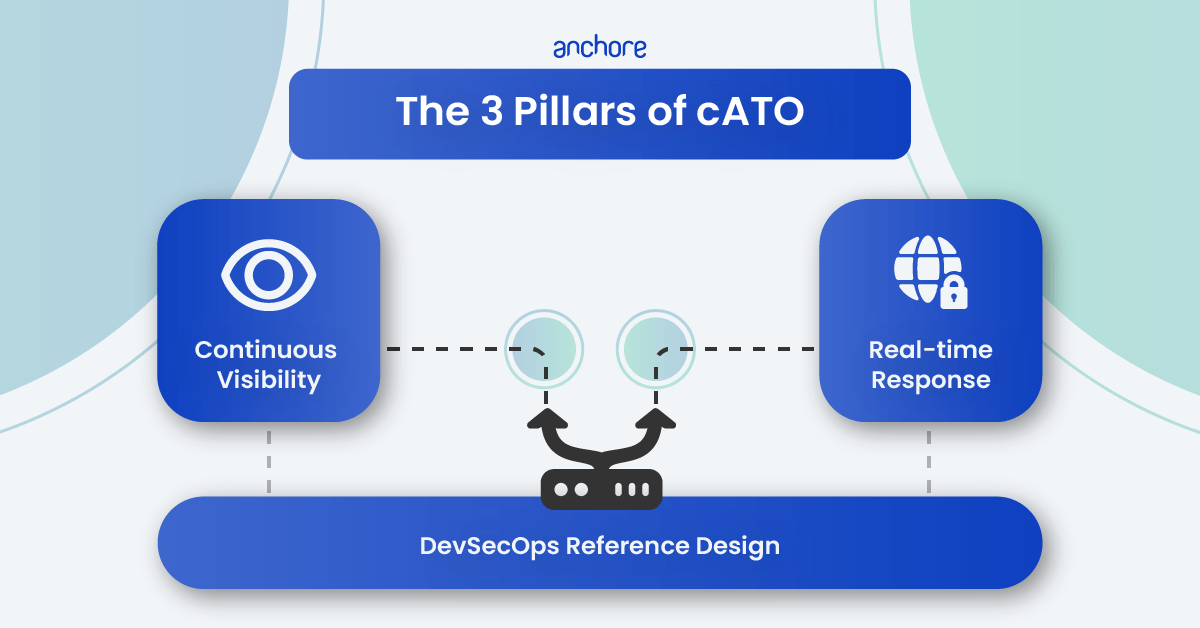
Achieve continuous ATO (cATO)
Fulfill the required capabilities of cATO more easily. Use automated security checks and policy enforcement to continuously monitor and assess security controls per the Risk Management Framework (RMF). Generate, store, and monitor SBOMs throughout the development lifecycle to ensure the security of the software supply chain. Leverage a centralized SBOM database to instantly triage the impact of zero-day vulnerabilities. Align with the DoD DevSecOps Reference Design and DoD Container Hardening Guide.

The Security Technical Implementation Guide (STIG) is a Department of Defense technical guidance standard that captures the cybersecurity requirements for a specific product. Achieving STIG compliance is complex and can be daunting. Download our in depth guide on best practices.