Software Supply Chain Security
Secure open source software dependencies.
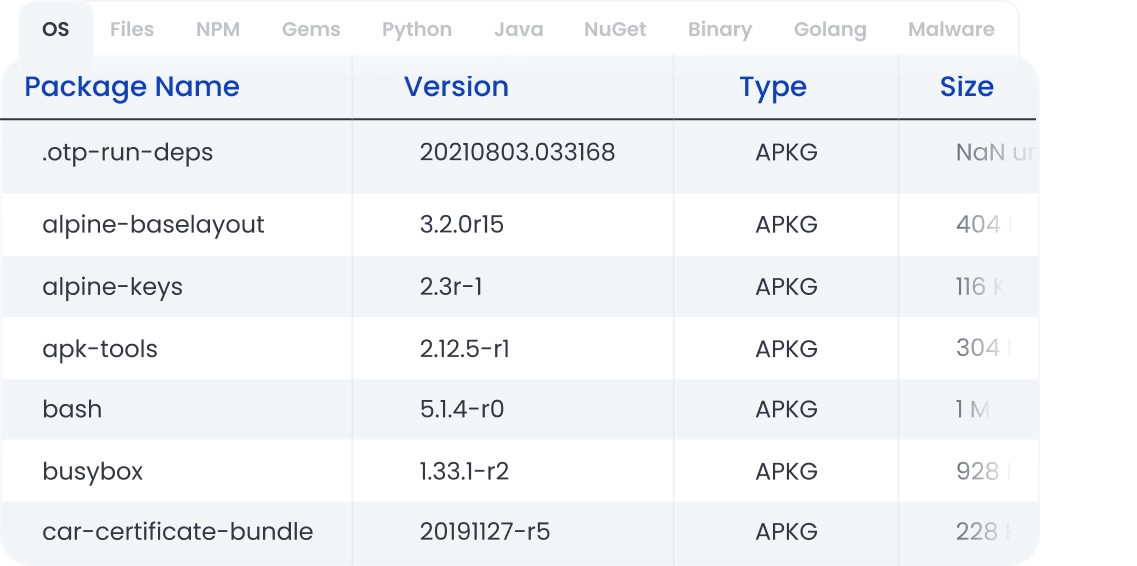
Easily track direct and transitive open source dependencies to identify and fix vulnerabilities early.
Benefits
SBOM management.
Generate, manage, and store SBOMs for the software you use and build. Leverage SBOMs to identify and track open source dependencies at scale. Ensure that open source components and their dependencies are compliant with all cybersecurity license requirements.
Vulnerability scanning.
Analyze and scan source code repositories, CI/CD pipelines, container registries, and container runtime environments for open source software vulnerabilities. Detect zero-day vulnerabilities and instantly identify which components and applications are impacted by simply re-analyzing your stored SBOMs — there’s no need to re-scan applications or cyber components.
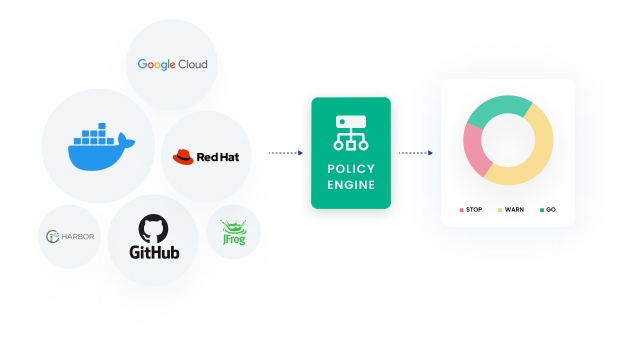
Policy enforcement.
Use out-of-the-box policies or create your own to ensure compliance with internal rules and industry cybersecurity standards. Trigger notifications and remediation workflows based on rules set through a policy engine. Block compromised open source software like Log4j from being deployed into production.
License compliance.
Identify open source licenses for both direct and transitive open source licenses. Define policy rules to notify of disallowed licenses. Customize policy gates to fail builds or prevent deployment into production.
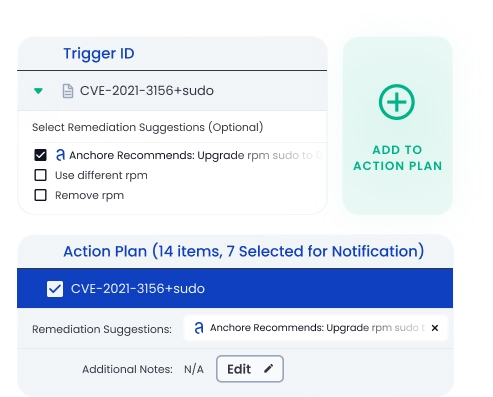
Streamline remediation.
Prioritize vulnerabilities based on severity, fix availability, or other customizable criteria. Deliver remediation recommendations that make it easy for developers to fix. Reduce noise with allowlists to stop alerts while they are being remediated.
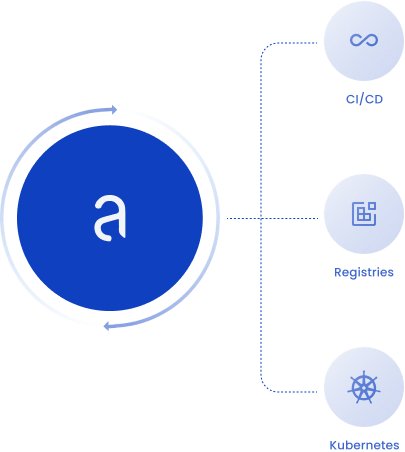
How open source security works in Anchore.

Inspect and secure workloads across the entire software supply chain
Integrations for streamlined open source security.

























Related resources.
Visually hidden 

Blog | Jun 14, 2022
3 Myths of Open Source Software Risk and the One Nobody Is Discussing
Read the Blog
Visually hidden 

Webinar | Feb 16, 2022
Best Practices for Securing Open Source Software for Enterprises
Watch the webinar
Visually hidden 

Blog | Oct 14, 2021
7 Tips to Create a DevSecOps Open Source Strategy
Read the Blog
Speak with our security experts
Learn how Anchore’s SBOM-powered platform can help secure your software supply chain.
