Satisfy FedRAMP vulnerability scanning requirements
Companies that sell cloud-based software to the US government must meet FedRAMP requirements, including for vulnerability scanning. When software is deployed via containers, organizations must meet additional FedRamp vulnerability scanning requirements for containers.
Anchore Enterprise provides out-of-the-box capabilities to help meet FedRAMP requirements:
- Vulnerability scanning with the latest vulnerability feeds
- Anchore Enterprise FedRAMP Policy Pack to validate controls
- STIG checks to validate hardened images
- Registry monitoring for automatic image scanning
- Central storage of Software Bills of Materials (SBOMs) to provide asset management and inventory reporting
- Monthly reporting of vulnerabilities for FedRAMP ConMon

5 Insider Tips for Federal Software Compliance
In this webinar we will draw from our experience and learnings from the Iron Bank approach to improve software visibility and supply chain security. Learn common security checks to help comply with any standard, ins and outs of SBOM creation and more.
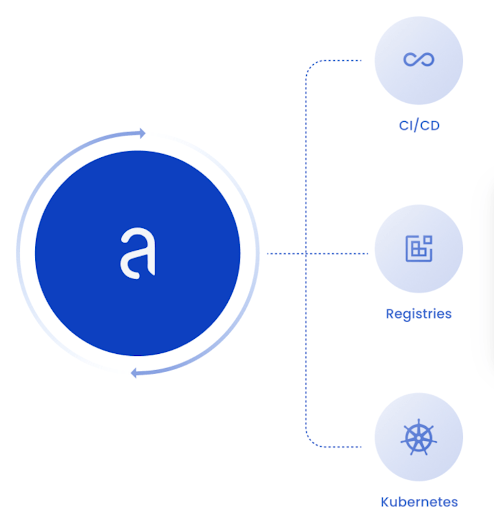
Vulnerability scanning for container images
Automate vulnerability scans in CI/CD pipelines, registries, and Kubernetes platforms to meet the FedRAMP 30-day scanning window. Harden container images by identifying malware, secrets, and security risks in addition to vulnerabilities. Performing STIG checks for container images.
Automate FedRAMP and NIST controls
Speed compliance with Anchore’s out-of-the-box policy packs for FedRAMP and NIST controls. Enforce FedRAMP Rev 4 and automate checks of containers and images from build to deployment. Pinpoint the exact control ID and container image for any failures. Demonstrate compliance with controls for NIST 800-53 and 800-190 and from the Secure Software Development Framework as codified in NIST 800-218.
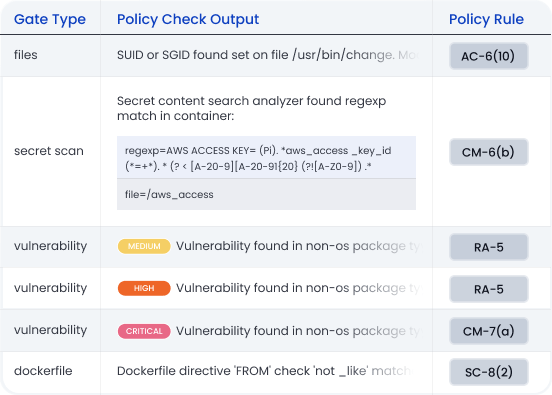
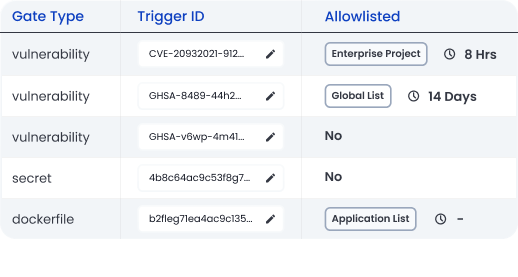
Manage vulnerability remediation
Add non-compliant findings to an allowlist with specified FedRAMP time limits. Set alerts to ensure vulnerabilities are remediated within required timelines. Evaluate exceptions and create a Plan of Action and Milestones (POAM) for remediation.
Registry monitoring
Automate continuous scanning of all registry images. Leverage Anchore’s admission controller to prevent unscanned or insecure images from being deployed in production.
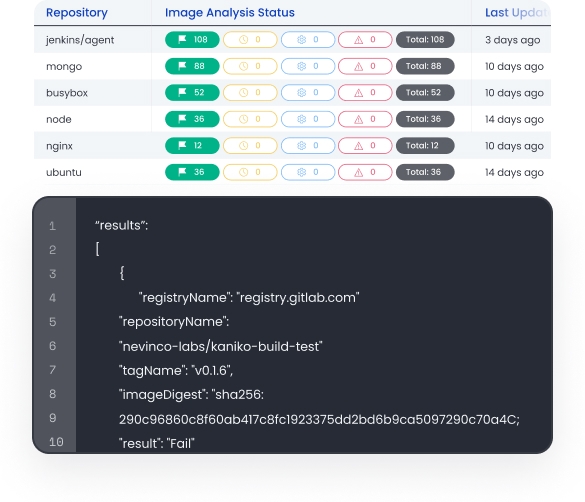
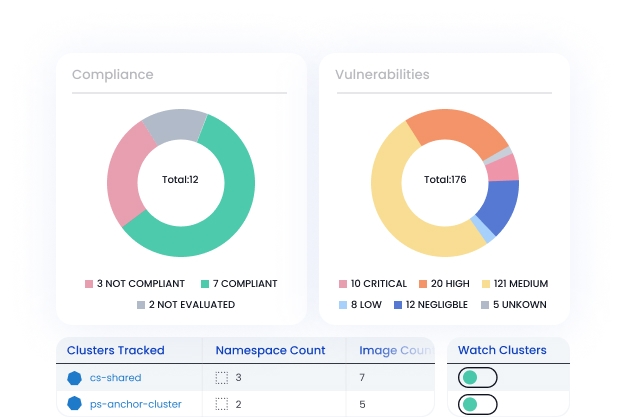
Continuous monitoring (ConMon) of production
Rely on continuous monitoring (ConMon) to scan Kubernetes production environments. Automatically inventory container images running in production, identify vulnerabilities, analyze FedRAMP controls, and alert on violations. Easily create monthly reports on vulnerabilities.
Streamline FedRAMP reporting
Deliver pass/fail reports for FedRAMP controls to your auditor. Demonstrate the controls you have in place and show any exceptions you have identified. Automate monthly vulnerability reports.

Download our checklist on how to meet FedRAMP vulnerability scanning requirements for containers today. You will learn about the new 30-day scanning window, determine the use of hardened base images and how to integrate scans across the container lifecycle.

