Anchore is excited to announce the official release of our integration with Azure DevOps. Azure DevOps is a powerful tool from Microsoft that allows developers to build and release production software. This integration with Anchore allows developers to seamlessly integrate security into their Azure DevOps pipelines with very little effort.
Anchore’s robust scanning brings not only vulnerability detection but policy enforcement for any application. All you need to do is add some simple YAML to your existing pipeline to create secure production software. Once the extension is installed into your organization, follow the steps below to get it added to any pipeline.
Step 1. Review the Existing Build and Release Pipeline
trigger:
- master
- dev
variables:
image_name: "localbuild/testimage"
tag: "ci"
stages:
- stage: Build
displayName: Build application container
jobs:
- job: Build
displayName: Docker Build
steps:
- task: Docker@2
inputs:
command: build
repository: "$(image_name)"
tags: "$(tag)"
- stage: Release
displayName: Release the application
...Right now this pipeline is simply using the Docker task to build a local container and then it will publish the container in the release stage (omitted for simplicity).
Step 2. Add the Anchore Scanner Plugin
The Anchore scanner will scan a locally built container so it can provide a decision point early in the pipeline. All that needs to happen is add the Anchore scanner plugin to the pipeline right after the build stage so it can scan the local image.
trigger:
- master
- dev
variables:
image_name: "localbuild/testimage"
tag: "ci"
stages:
- stage: Build
displayName: Build and scan with Anchore
jobs:
- job: Build
displayName: Build and Scan
steps:
- task: Docker@2
inputs:
command: build
repository: "$(image_name)"
tags: "$(tag)"
- task: Anchore@0
inputs:
image: "$(image_name):$(tag)"
customPolicyPath: ".anchore/policy.json"
dockerfile: Dockerfile
- script: |
echo $(policyStatus)
echo $(billOfMaterials)
cat $(billOfMaterials)
echo $(vulnerabilities)
cat $(vulnerabilities)
displayName: Print scan artifactsIn this example, a custom policy is provided alongside the code and it is referenced inside the scan so it can enforce the security required for production software.
Step 3. Run the Pipeline
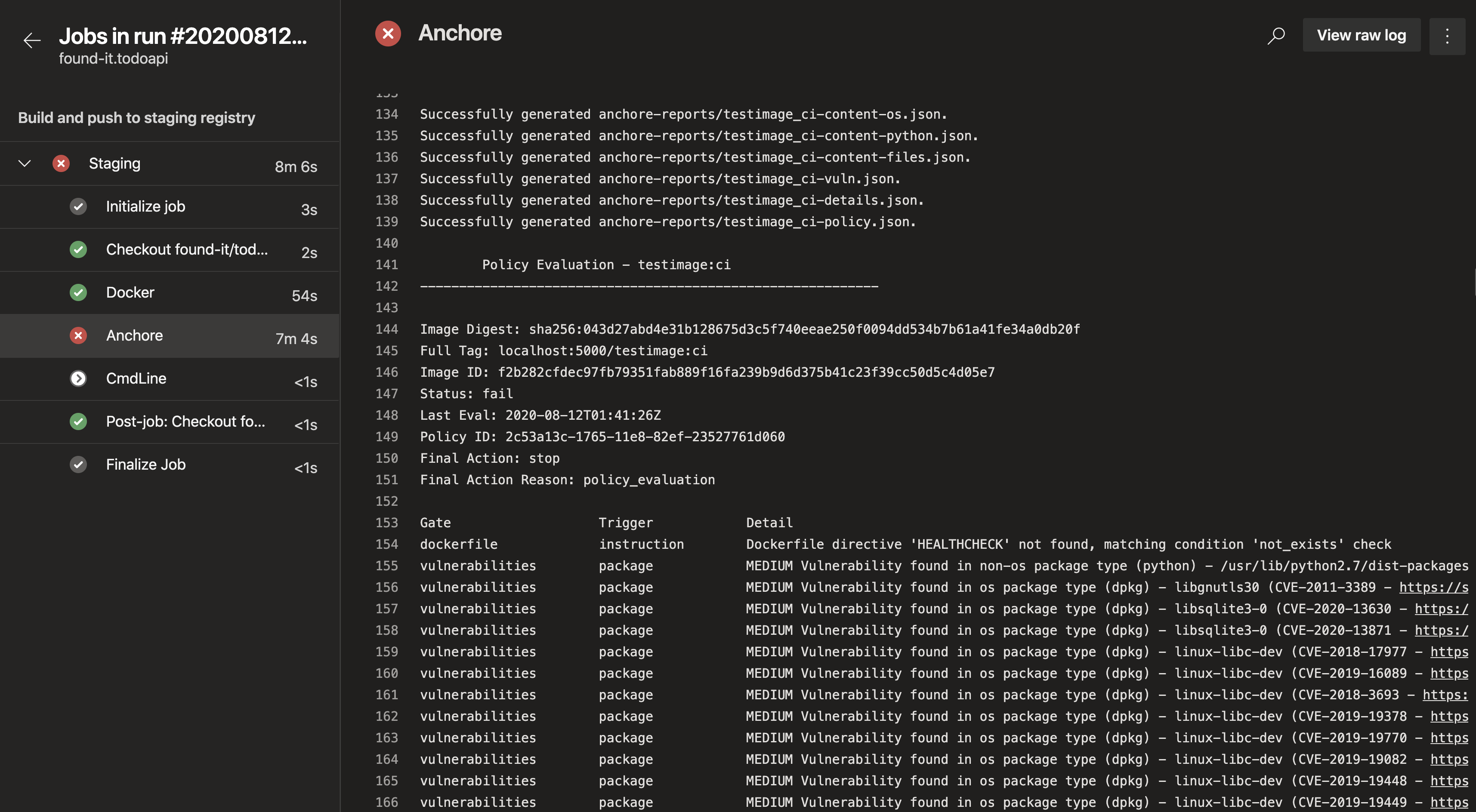
Run the pipeline like normal and watch Anchore do its work scanning the local image. Once Anchore has scanned the image, the results of the policy evaluation will be displayed in the terminal along with a table of the discovered vulnerabilities. You can also reference the outputs of Anchore as pipeline variables so you can keep the scan results or policy evaluation in a database for further inspection.
Step 4. Customize the Extension
The extension can be customized fully to fit the needs of the pipeline, just reference the documentation on the extension page for more in-depth detail about the input parameters. It also does not require access to Anchore Engine or Enterprise. The plugin comes with all the capabilities of Anchore wrapped inside of it including ways to provide custom policies and change the behavior of the pipeline based on results.
Azure DevOps is a powerful tool used by many development teams to build and publish production-grade software. With the integration of Anchore into the Azure DevOps environment, producing secure software becomes even more reliable. Anchore enforces consistent security policy for every run of the pipeline and will ensure that software that is not secure never makes it to production.




