Platform | Enforce
Anchore Enforce
Choose your policy and enforce it at every stage of the SDLC. Raise alerts for developers, show trends to the CISO, and generate evidence for auditors.

Compliance Management for US Government Federal standards
Companies that sell software to governments or regulated industries need robust software security programs and soon be required to attest to the US government that they follow secure software development practices. Anchore Enterprise provides NIST compliance tools to automate various standards and controls, including NIST 800-171, NIST 800-53, NIST 800-190, and NIST 800-218 Secure Software Development Framework.
Enforce & Prove Compliance
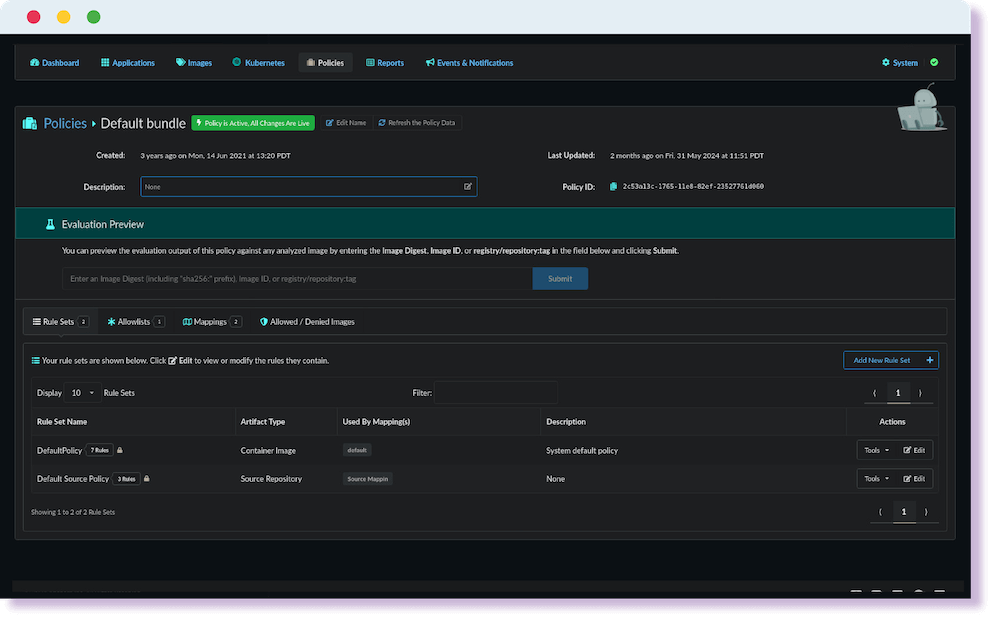
FedRAMP, NIST, DISA, and DOD policy packs.
Deploy a ready to use policy to achieve compliance with a variety of federal standards. Each rule is mapped to the specific control version for easy report and evidence generation. Shift your compliance checks “left” and have developers fix issue before deployment.
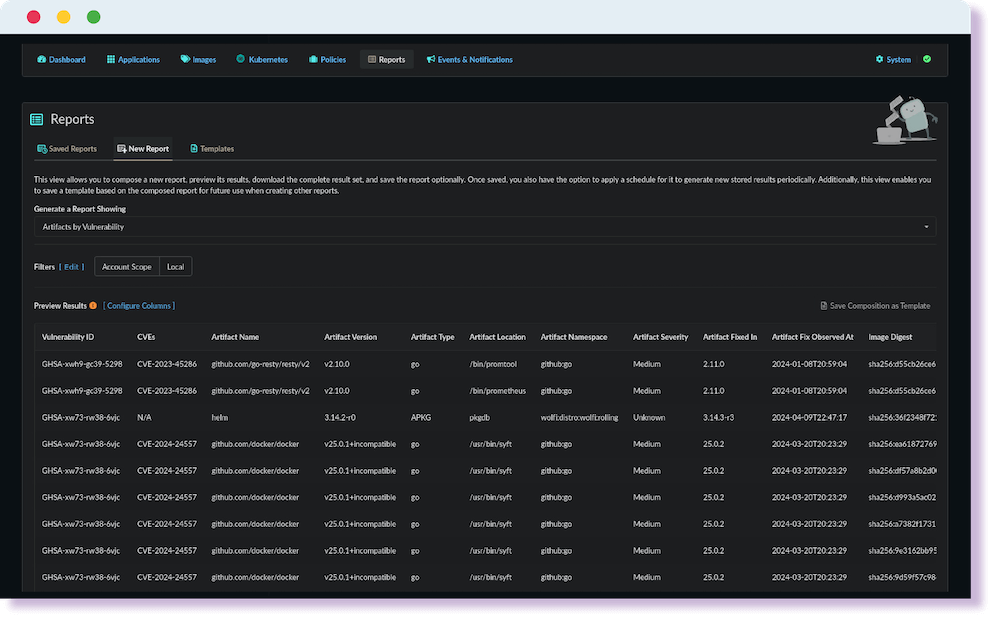
Flexible Reporting Options
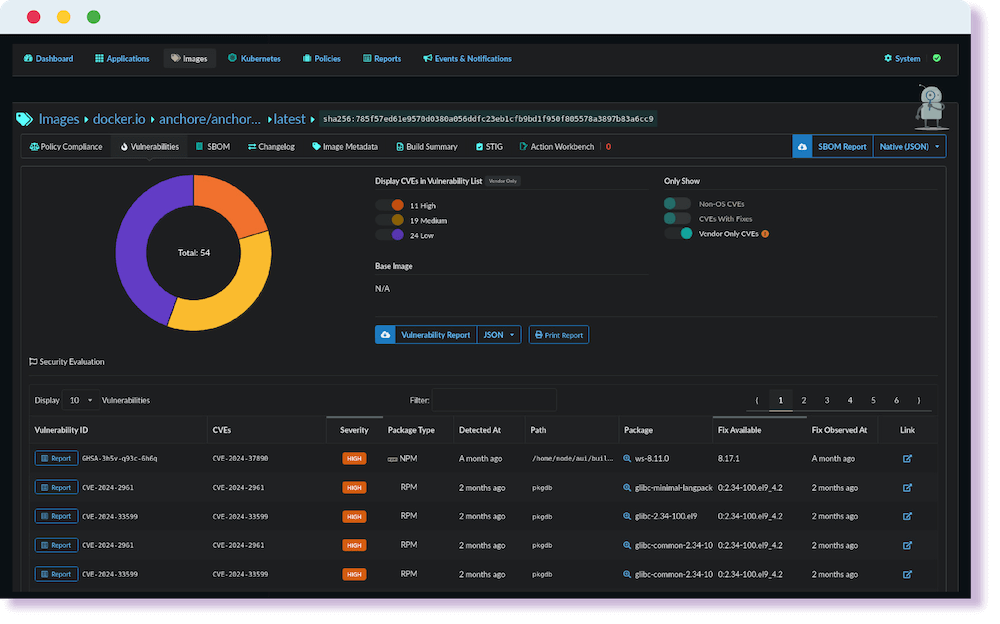
Produce reports from the simple to the detailed with Anchore’s powerful reporting engine. Choose from a range of default reports providing an overview of risk across all of your sites to customized reports which focus on specific registries, repos, or runtime environments.

Runtime Context
Verify the compliance status of your production applications with a real time view of the cluster and namespaces running your containers. Zero in on the specific base images causing out of compliance alerts.
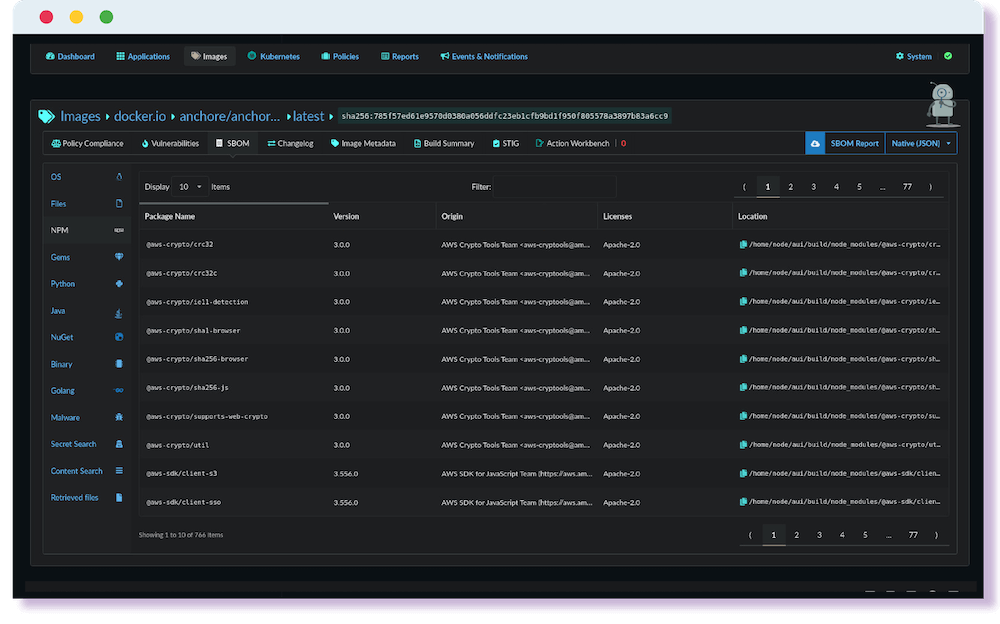
License Management
Prevent the use of copyleft licenses or warn on the use of unapproved licenses. Search for software that has been relicensed to prevent commercial risk.
Dockerfile Controls
Limit the use of instructions which introduce risk to container image builds. Prevent the use of unapproved packages or binaries. Disable network access or effective users with elevated privileges.
More Capabilities.
Base Image Management
Ensure only approved golden images are used as base images. Prevent the use of unauthorized operating systems or find the use of distributions approaching or past the end of life support.
Content and Metadata Inspection
Anchore can look at every piece of metadata for any file on the filesystem to: detect files with global read or write permissions or elevated privileges (SUID); ensure file hashes map to known good signatures; or, determine if mandatory files are missing or typosquatting files are present. You can go further and look for specific configuration strings inside files to ensure that values are set according to best practices.
Policy as Code
Every policy rule configured in Anchore is stored in an easy to edit JSON file allowing GitOps workflows around policy management and synchronization across deployments.
FAQs
We provide policy packs that cover FedRAMP v5, NIST 800-53, 800-190, DISA, and Docker CIS. An Anchore Enterprise deployment also allows you to comply with the NIST 800-219 (Secure Software Development Framework) attestation requirements.
All Anchore policy rules are stored in a simple JSON format that can be edited by a human or managed programmatically via Git.
Related resources.
Visually hidden 

May 24, 2024
How Cisco Umbrella Achieved FedRAMP Compliance in Weeks
Download the Case Study
Visually hidden 

Apr 24, 2024
SSDF Attestation 101: A Practical Guide for Software Producers
Download the White Paper
Visually hidden 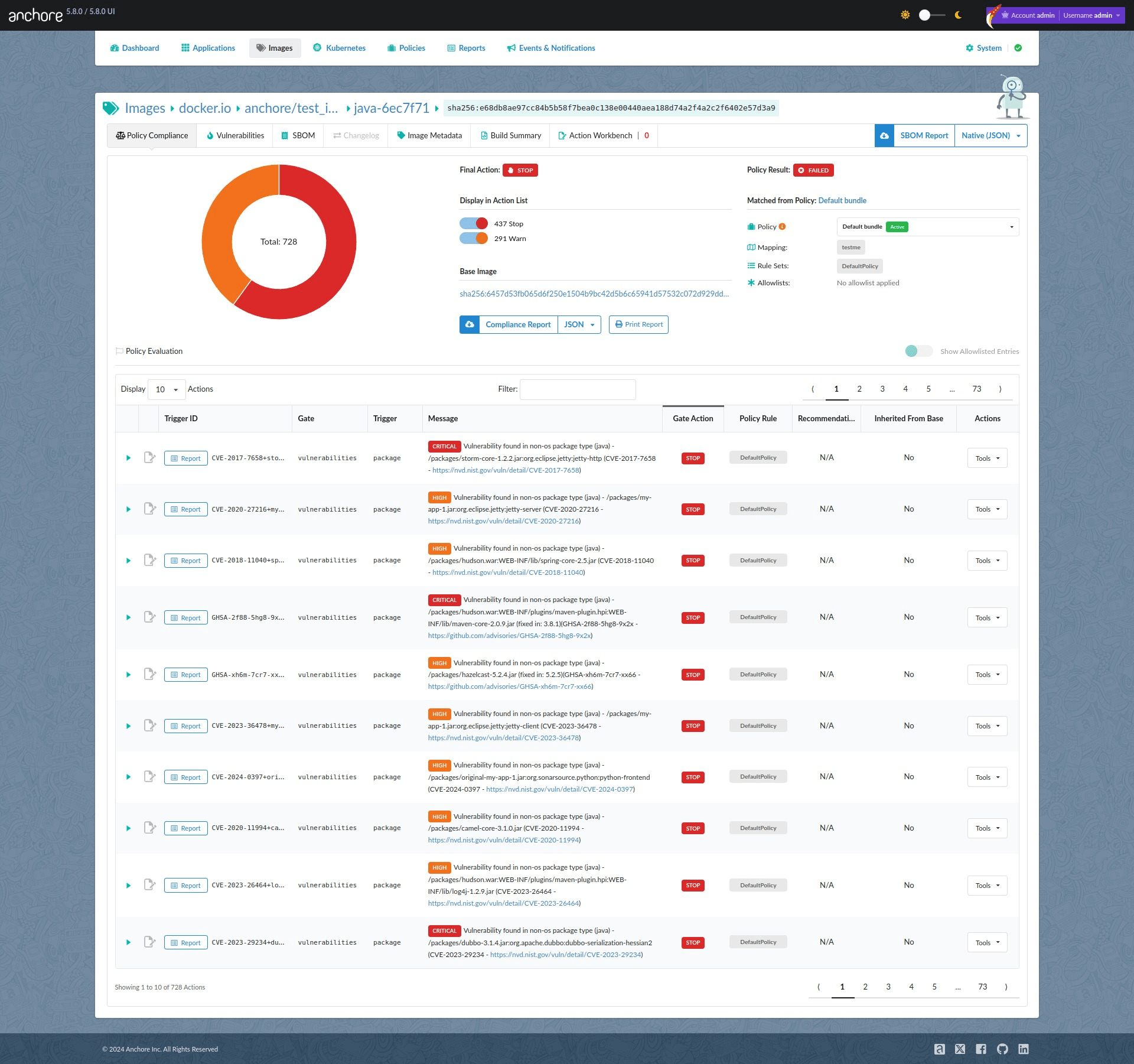

Jul 31, 2024
Anchore Enterprise 5.8 Adds KEV Enrichment Feed
Read the Blog
Speak with our security experts
Learn how Anchore’s SBOM-powered platform can help secure your software supply chain.

