At their recent Satellite event in early May, GitHub released a powerful new addition to their increasingly robust set of security and automation features within GitHub Advanced Security, called code scanning. At a high level, this new feature brings static code analysis (based on the CodeQL technology acquired from Semmle last year), with a focus on identifying common and known security flaws in source code patterns, directly into the software development lifecycle (SDLC). Along with GitHub Actions, users are now even closer to using these native tools to manage their end-to-end ‘commit-to-release’ process, including security checks along the way.
At Anchore, we’re a firm believer in the concepts of identifying security issues as far ‘left’ and as part of as many stages of the SDLC as possible, which drastically reduces the impact of a security problem when compared to discovering an issue after software is released (or worse, deployed). Because of this alignment of purpose, we were excited to dive into this new feature in collaboration with our partners at GitHub, and explore ways in which we could potentially leverage this new capability with our own technology for scanning container images for security flaws, using the same framework and management tools that GitHub is providing for source code analysis.
Today, we’re happy to announce that Anchore’s GitHub Scan Action now supports integration with GitHub’s code scanning feature on eligible repositories. With this new capability, users can leverage both GitHub’s CodeQL-based security analysis to their action flows, and also now include another vital security step with Anchore that scans and reports on any security, compliance and best-practice flaws that may be present in a final container build artifact. By adding both steps, users are able to not only get high quality source code security scans, but also be assured that any container image that is built from the source code (often a final step that produces the actual artifact that would be deployed) is also scanned and secured. At Anchore, we believe that this is an important step that must be considered as the construction of container images often brings in additional code, dependencies, and configurations that are not directly present in the source code itself.
Anchore Scan Action
The Anchore Scan Action is a step that any GitHub Actions user can include in their existing workflows. This Action provides a vulnerability scan and/or an Anchore policy evaluation against a locally generated container artifact. We won’t go into the full details of the Anchore Scan Action here, but please refer to the Anchore Scan Action page for more information on configuring and including this action. For the purposes of this discussion, the high level idea of the Anchore Scan Action is that it takes as input a reference to a container image, performs its security and compliance scan, and generates JSON reports for the container image software bill of materials (SBOM), vulnerabilities that have been discovered as present in the container image, and a full (customizable) Anchore policy evaluation report.
One of the powerful new features of the GitHub code scanning feature is that the system supports the ability for third-party tools (like Anchore!) to produce results that live alongside the built in CodeQL reports. For the latest release of the Anchore Scan Action, we’ve integrated with this capability - the same container vulnerability scanning step now can generate a document (in SARIF format) that encodes Anchore’s vulnerability report data in a form that can then be uploaded back to GitHub, resulting in a security report that lives alongside the new code scanning alerts. This way, findings from both the CodeQL source code scanning step and the Anchore container image scanning step can be reviewed and managed using a common interface.
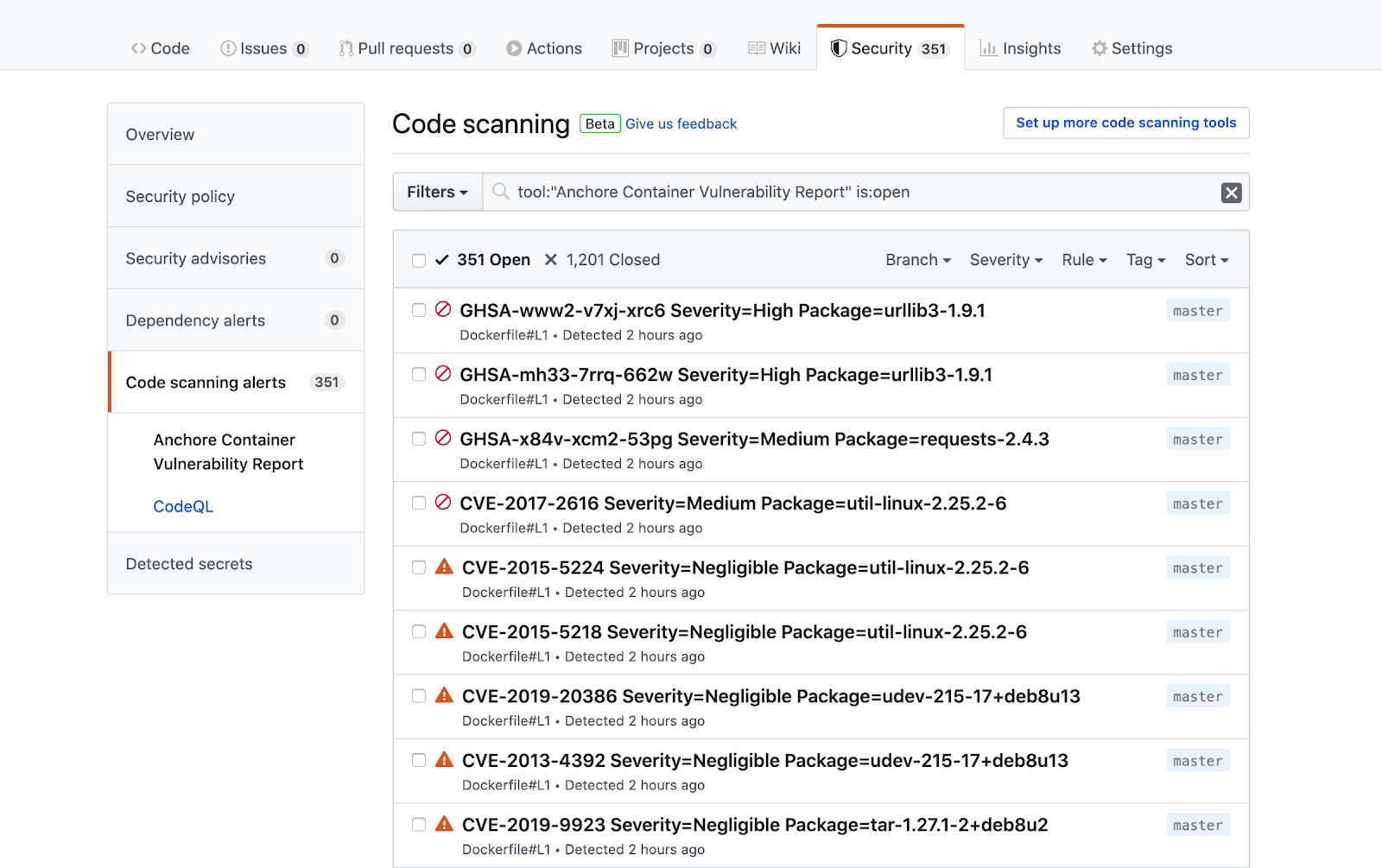
In the screenshot above, we’re looking at an example of a workflow that checks out code, performs a CodeQL scan, builds a container image from the code, performs an Anchore scan, and completes. Once the run is finished, we see that the report section of the security tab in GitHub now includes both a CodeQL section as well as an Anchore Container Scan section, listing all of the vulnerabilities that Anchore discovered as present in the built container image. Clicking into one of the findings, we’ll get even more detail:
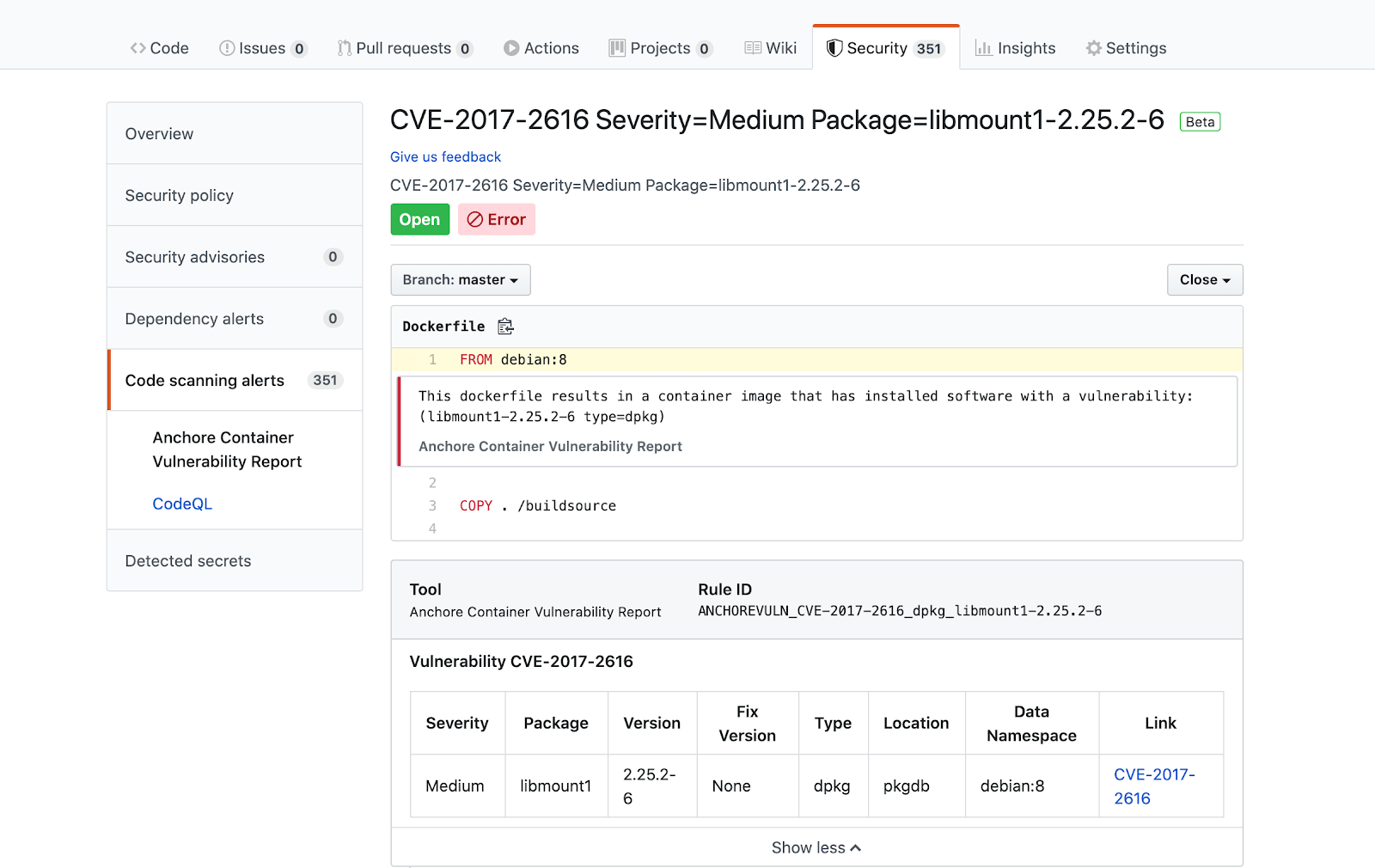
Here, we can see that the Anchore scan result includes information about the vulnerability identifier, severity, the vulnerable software artifact metadata (name, location, type and version) and a link to the upstream vulnerability information itself.
Example Workflow: Automating a Scan
Through GitHub Actions and an increasing tool-chest of powerful security and quality tools, GitHub has made it extremely easy to add this type of scanning and reporting to your existing workflow. Below is a short example of a workflow YAML definition that implements the steps that produced the screenshots in the previous section. If you’re already using the Anchore Scan Action, then the only changes required are to enable the ACS report generation feature, and add an ‘upload’ step at the end of the scan.
Example Action YAML:
name: "Run Anchore Scan Action (ACS SARIF Demo)"
on: [push]
jobs:
CodeQL-Analysis:
runs-on: ubuntu-latest
steps:
- name: Checkout the code
uses: actions/checkout@v2
# Initializes the CodeQL tools for scanning.
- name: Initialize CodeQL
uses: github/codeql-action/init@v1
# Override language selection by uncommenting this and choosing your languages
# with:
# languages: go, javascript, csharp, python, cpp, java
- name: Perform CodeQL Analysis
uses: github/codeql-action/analyze@v1
Anchore-Scan-Action:
runs-on: ubuntu-latest
steps:
- name: Checkout the code
uses: actions/checkout@v2
- name: Build the Docker image
run: docker build . --file Dockerfile --tag localbuild/testimage:latest
- name: Run the local anchore scan action itself with sarif generation enabled
uses: anchore/scan-action@v1
with:
image-reference: "localbuild/testimage:latest"
debug: true
acs-report-enable: true
acs-report-severity-cutoff: "Medium"
- name: Upload Anchore Scan ACS Report
uses: github/codeql-action/upload-sarif@v1
with:
sarif_file: results.sarif
Summary and Further Information
This new feature within GitHub Advanced Security is truly exciting for us at Anchore - as more and more processes and best practices continue to favor a ‘shift left’ mindset (something that has been a core focus of Anchore technology throughout its history), we’re looking forward to continuing to work closely with GitHub and the community to bring fully featured security tooling right into your automated workflows quickly and easily.
For more information on the above topics, please see the following links:



